Blog
The recent wave of AI-supply chain attacks and quantum-computing threats demonstrate that third-party risk has evolved dramatically. In today's hyper-connected digital ecosystem, your attack surface now includes every vendor in your AI training data pipeline, cloud infrastructure, and technology st...
Wendy Dika
04.11.25 01:59 PM - Comment(s)
From ransomware crippling banking operations to data breaches derailing a promising startup, the stakes have never been higher. For many organizations, the critical question isn't if they need executive-level cybersecurity leadership, but what form that leadership should take.
The...
Wendy Dika
01.11.25 02:07 PM - Comment(s)
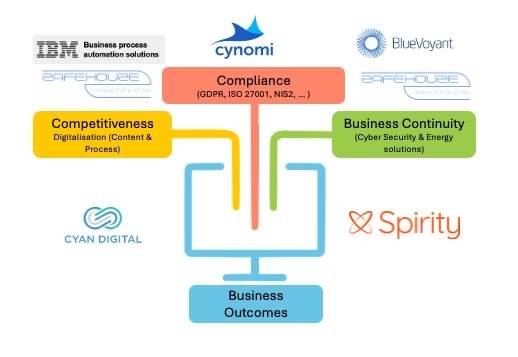
Today, the world is hyperconnected and African businesses are facing a growing mix of digital challenges. From rising compliance requirements to complex cyber threats, to operational disruptions. That’s where Lifu Technologies steps in.
WHO ARE WE?
Lifu Technologies is a forward-...
Wendy Dika
30.10.25 03:47 PM - Comment(s)
Cynomi streamlines cybersecurity for vCISOs, automating compliance, assessments, and reporting across clients with real-time insights and audit ready results.
Chinonso Eboh
05.08.25 03:52 PM - Comment(s)